iPhone users are being urged by the FBI to immediately delete a specific text message that could install malware and compromise their devices, according to a recent public service announcement. The alert focuses on a sophisticated smishing (SMS phishing) campaign targeting mobile devices, and highlights the potential for significant financial and data loss if users interact with the malicious text. The FBI warns that clicking on links within these texts can lead to malware installation, enabling cybercriminals to steal personal information, banking credentials, and other sensitive data.
The FBI’s warning, issued in response to a growing wave of sophisticated cyberattacks, emphasizes the importance of vigilance and caution when receiving unsolicited text messages. The agency has observed a significant increase in smishing campaigns designed to exploit vulnerabilities in mobile operating systems, particularly those affecting Apple’s iOS. These attacks often involve deceptive tactics, such as impersonating legitimate organizations or offering enticing rewards, to trick users into clicking on malicious links.
The specific type of malware being distributed through these smishing campaigns varies, but common threats include banking trojans, spyware, and ransomware. Banking trojans are designed to steal financial information, such as usernames, passwords, and credit card details. Spyware can track a user’s activity, including their location, browsing history, and communications. Ransomware encrypts a user’s data and demands a ransom payment for its release.
“Cybercriminals are increasingly targeting mobile devices through smishing campaigns,” said an FBI spokesperson. “These attacks can have devastating consequences for individuals and organizations alike. It is crucial that users take steps to protect themselves by being cautious about the text messages they receive and avoiding clicking on suspicious links.”
The FBI advises iPhone users to take the following steps to protect themselves from smishing attacks:
-
Delete Suspicious Texts: If you receive a text message from an unknown sender or one that seems suspicious, delete it immediately. Do not click on any links or provide any personal information.
-
Verify Sender Identity: If you receive a text message from a company or organization, verify the sender’s identity by contacting them directly through a known phone number or website. Do not use the contact information provided in the text message.
-
Enable Spam Filtering: Enable spam filtering on your mobile device to help block unwanted text messages.
-
Update Software: Keep your mobile device’s operating system and apps up to date with the latest security patches.
-
Use Strong Passwords: Use strong, unique passwords for all of your online accounts.
-
Enable Two-Factor Authentication: Enable two-factor authentication for all of your online accounts to add an extra layer of security.
-
Be Skeptical: Be skeptical of any text message that asks you to provide personal information or click on a link.
-
Report Suspicious Activity: Report any suspicious activity to the FBI’s Internet Crime Complaint Center (IC3).
The threat posed by smishing campaigns is not limited to individuals. Businesses and organizations are also at risk. Cybercriminals can use smishing to gain access to corporate networks and steal sensitive data. The FBI advises businesses to educate their employees about the risks of smishing and to implement security measures to protect against these attacks.
“Businesses should train their employees to recognize and avoid smishing attacks,” said the FBI spokesperson. “They should also implement security measures such as mobile device management (MDM) software to help protect against malware and data loss.”
The rise in smishing attacks reflects a broader trend of cybercriminals targeting mobile devices. Mobile devices have become increasingly popular targets due to their widespread use and the large amount of personal and financial information they contain. In addition, mobile devices often have weaker security than desktop computers, making them easier to compromise.
The FBI is working with law enforcement agencies and cybersecurity experts to combat smishing and other cybercrimes. The agency encourages individuals and businesses to report any suspicious activity to the IC3. By working together, the FBI and the public can help to protect against these threats.
The evolving nature of cyber threats necessitates continuous vigilance and proactive measures. As cybercriminals develop increasingly sophisticated tactics, it is essential for users to stay informed and adopt best practices to safeguard their devices and data. The FBI’s warning serves as a critical reminder of the ongoing risks and the importance of taking immediate action to mitigate potential harm.
The FBI’s Internet Crime Complaint Center (IC3) is a crucial resource for reporting cybercrimes and receiving updates on emerging threats. By reporting suspicious activity, individuals and organizations can contribute to the collective effort to combat cybercrime and protect the digital ecosystem. The IC3 provides a platform for sharing information and coordinating law enforcement efforts, ultimately enhancing the effectiveness of investigations and prosecutions.
The increasing sophistication of smishing campaigns highlights the need for advanced security solutions, such as mobile threat defense (MTD) platforms. MTD solutions provide real-time protection against a wide range of mobile threats, including malware, phishing attacks, and network intrusions. These solutions can detect and prevent malicious activity before it can compromise a device or network, providing an additional layer of security beyond the built-in features of mobile operating systems.
Furthermore, the FBI emphasizes the importance of promoting cybersecurity awareness among all users, regardless of their technical expertise. Education and training programs can help individuals and organizations understand the risks of cybercrime and adopt best practices for protecting themselves. These programs should cover topics such as identifying phishing emails, using strong passwords, and enabling two-factor authentication.
The FBI’s warning also underscores the critical role of mobile device manufacturers and software developers in enhancing the security of mobile devices. These companies have a responsibility to develop and implement security features that protect users from cyber threats. This includes regularly releasing security updates and patches, providing robust anti-malware protection, and implementing strong authentication mechanisms.
The proliferation of mobile devices has created a vast attack surface for cybercriminals. As more and more people rely on their smartphones and tablets for communication, entertainment, and financial transactions, the potential for harm from cyberattacks continues to grow. The FBI’s warning serves as a call to action for individuals, businesses, and government agencies to work together to address the challenges of mobile security and protect against the evolving threat landscape.
The FBI continues to monitor cyber threats and provide guidance to the public on how to stay safe online. The agency encourages individuals and businesses to visit its website and social media channels for the latest information and resources. By staying informed and taking proactive measures, users can significantly reduce their risk of becoming victims of cybercrime.
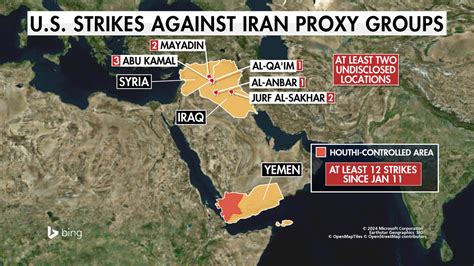
The impact of smishing attacks can be far-reaching, affecting not only individuals but also the broader economy and national security. Cybercriminals can use stolen information to commit identity theft, fraud, and other crimes. They can also use compromised devices to launch attacks against critical infrastructure and government networks. The FBI’s efforts to combat smishing and other cybercrimes are essential for protecting the nation’s economy and security.
In conclusion, the FBI’s warning about the smishing campaign targeting iPhone users underscores the importance of vigilance and caution when receiving unsolicited text messages. By following the FBI’s recommendations, users can significantly reduce their risk of becoming victims of these attacks. The agency’s ongoing efforts to combat cybercrime are essential for protecting individuals, businesses, and the nation as a whole. It is crucial to delete suspicious texts immediately, verify sender identities, enable spam filtering, update software, use strong passwords, enable two-factor authentication, be skeptical, and report suspicious activity to the FBI’s Internet Crime Complaint Center (IC3).
Expanded Context and Background Information
The FBI’s recent warning about smishing attacks targeting iPhone users is not an isolated incident but rather a part of a larger, concerning trend in the cybersecurity landscape. Smishing, a portmanteau of “SMS” and “phishing,” is a form of social engineering that uses deceptive text messages to trick individuals into divulging sensitive information, downloading malware, or taking actions that compromise their security. These attacks have become increasingly prevalent and sophisticated, posing a significant threat to individuals, businesses, and even national security.
The rise of smishing can be attributed to several factors. First, mobile devices have become ubiquitous, with billions of people around the world relying on smartphones and tablets for communication, entertainment, and financial transactions. This widespread adoption has created a vast attack surface for cybercriminals, who see mobile devices as an easy target for exploitation.
Second, mobile devices often have weaker security than traditional desktop computers. While mobile operating systems like iOS and Android have built-in security features, they are not always sufficient to protect against the latest threats. In addition, many users fail to update their devices regularly, leaving them vulnerable to known security flaws.
Third, smishing attacks are often more effective than traditional phishing attacks that target email. People tend to trust text messages more than emails, making them more likely to fall for deceptive tactics. In addition, text messages are often displayed on mobile devices with limited screen space, making it difficult to spot red flags such as suspicious links or grammatical errors.
The consequences of smishing attacks can be severe. Victims can suffer financial losses, identity theft, and damage to their reputation. Businesses can experience data breaches, system downtime, and legal liabilities. In some cases, smishing attacks can even be used to compromise critical infrastructure and government networks.
The FBI’s warning highlights the importance of taking proactive steps to protect against smishing attacks. These steps include:
-
Being skeptical of unsolicited text messages: Always be wary of text messages from unknown senders or those that seem too good to be true.
-
Avoiding clicking on links in text messages: Never click on links in text messages unless you are absolutely sure of the sender’s identity and the link’s destination.
-
Verifying the sender’s identity: If you receive a text message from a company or organization, verify the sender’s identity by contacting them directly through a known phone number or website.
-
Enabling spam filtering: Enable spam filtering on your mobile device to help block unwanted text messages.
-
Updating software regularly: Keep your mobile device’s operating system and apps up to date with the latest security patches.
-
Using strong passwords: Use strong, unique passwords for all of your online accounts.
-
Enabling two-factor authentication: Enable two-factor authentication for all of your online accounts to add an extra layer of security.
-
Reporting suspicious activity: Report any suspicious activity to the FBI’s Internet Crime Complaint Center (IC3).
In addition to these individual measures, businesses and organizations should also implement security policies and training programs to protect against smishing attacks. These policies should address topics such as mobile device usage, data security, and incident response. Training programs should educate employees about the risks of smishing and how to identify and avoid these attacks.
The fight against smishing requires a collaborative effort from individuals, businesses, government agencies, and technology providers. By working together, we can reduce the impact of these attacks and protect ourselves from the growing threat of cybercrime.
Expanded Information on Malware Types Distributed via Smishing
The FBI warning specifically highlights the danger of malware being installed through these smishing campaigns. Understanding the types of malware distributed and their potential impact is crucial for iPhone users. Here’s a more detailed breakdown:
-
Banking Trojans: These malicious programs are designed to steal banking credentials, credit card information, and other sensitive financial data. They often masquerade as legitimate banking apps or services to trick users into entering their login details. Once installed, the Trojan can monitor the user’s activity, intercept SMS messages containing two-factor authentication codes, and even initiate fraudulent transactions without the user’s knowledge. The financial impact of banking Trojans can be devastating, leading to significant losses for individuals and businesses.
-
Spyware: Spyware is a type of malware that secretly monitors and collects information about a user’s activity. This information can include browsing history, location data, call logs, text messages, and even keystrokes. Spyware can be used for a variety of malicious purposes, such as stealing personal information, tracking a user’s movements, and eavesdropping on their conversations. The privacy implications of spyware are profound, as it can expose highly sensitive personal information to unauthorized parties.
-
Ransomware: Ransomware encrypts a user’s data and demands a ransom payment for its release. This type of malware can be particularly damaging, as it can render a device unusable and cause significant data loss. Ransomware attacks have become increasingly common in recent years, targeting individuals, businesses, and even critical infrastructure. The financial cost of ransomware attacks can be substantial, including ransom payments, recovery expenses, and lost productivity. While the FBI generally advises against paying ransoms, the decision to pay is often a difficult one, particularly for businesses that rely on access to their data.
-
Remote Access Trojans (RATs): RATs allow cybercriminals to remotely control an infected device. This control can include accessing files, installing software, monitoring activity, and even using the device’s camera and microphone. RATs can be used for a variety of malicious purposes, such as stealing data, launching attacks against other devices, and spying on the user. The potential for abuse with RATs is significant, as they give attackers complete control over the victim’s device.
-
Adware: While often less malicious than other types of malware, adware can still be disruptive and annoying. Adware displays unwanted advertisements on a device, often in the form of pop-ups or banners. It can also redirect users to malicious websites or track their browsing activity. While adware may not directly steal personal information or encrypt data, it can degrade the user experience and potentially expose them to other threats.
The specific type of malware distributed through smishing campaigns can vary depending on the attacker’s goals. However, the common thread is that these programs are designed to exploit vulnerabilities in mobile devices and compromise the user’s security. By being aware of the different types of malware and their potential impact, iPhone users can take steps to protect themselves from these threats.
Technical Details and Vulnerabilities Exploited
While the FBI warning doesn’t explicitly detail the specific technical vulnerabilities being exploited in these smishing campaigns, understanding the common techniques used can provide further insight:
-
Social Engineering: This is the cornerstone of nearly all smishing attacks. Attackers craft messages that prey on human psychology, using tactics like urgency, fear, greed, or trust to manipulate users into clicking malicious links or providing sensitive information. For example, a message might claim that a user’s account has been compromised and they need to verify their information immediately, or that they’ve won a prize and need to claim it by clicking a link.
-
Link Masking: Attackers often use link shortening services (like bit.ly) or URL encoding to hide the true destination of a malicious link. This makes it difficult for users to identify suspicious links, as they don’t reveal the actual website they will be directed to. Hovering over a link (on a computer) can reveal the true destination, but this isn’t easily possible on mobile devices.
-
Exploiting Mobile Operating System Vulnerabilities: In some cases, smishing attacks can exploit vulnerabilities in the mobile operating system itself to install malware or gain unauthorized access to the device. These vulnerabilities can be specific to certain versions of iOS or Android, and are often patched in security updates. This is why it’s critical to keep your device’s software up to date.
-
Configuration Profile Attacks (iOS): iOS devices can be configured using “configuration profiles,” which allow administrators to manage device settings and install apps. Malicious actors can create fake configuration profiles that appear legitimate but actually install malware or change device settings to compromise security. Users are often tricked into installing these profiles through social engineering.
-
SMS Spoofing: While becoming increasingly difficult, SMS spoofing allows attackers to send text messages that appear to come from a different phone number. This can be used to impersonate legitimate organizations or individuals, making it more likely that users will trust the message and click on malicious links.
-
Cross-Site Scripting (XSS) and Other Web Vulnerabilities: When a user clicks on a malicious link in a smishing message, they may be directed to a website that contains XSS vulnerabilities or other web security flaws. These vulnerabilities can allow attackers to inject malicious code into the website, which can then be used to steal cookies, redirect users to phishing pages, or install malware on their devices.
-
Zero-Day Exploits: In rare but highly dangerous cases, smishing attacks can leverage zero-day exploits, which are vulnerabilities that are unknown to the software vendor and have not yet been patched. These exploits can be extremely effective, as there are no defenses against them until a patch is released.
It’s important to note that Apple has implemented various security measures in iOS to protect against these types of attacks. However, cybercriminals are constantly developing new and sophisticated techniques to circumvent these defenses. Staying informed about the latest threats and following the FBI’s recommendations is crucial for protecting your iPhone from smishing attacks.
Frequently Asked Questions (FAQ)
Q1: What is smishing, and how does it differ from phishing?
A1: Smishing is a type of cyberattack that uses deceptive text messages (SMS) to trick individuals into divulging sensitive information, downloading malware, or taking actions that compromise their security. It’s a form of phishing, but instead of using email, it utilizes text messages. Phishing, in general, refers to fraudulent attempts to obtain sensitive information such as usernames, passwords, and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Smishing specifically leverages the SMS platform.
Q2: What types of information can cybercriminals steal through smishing attacks?
A2: Cybercriminals can steal a wide range of information through smishing attacks, including:
- Personal Information: Names, addresses, phone numbers, email addresses, dates of birth, Social Security numbers.
- Financial Information: Bank account numbers, credit card numbers, debit card numbers, usernames, passwords, PINs.
- Login Credentials: Usernames and passwords for various online accounts, such as email, social media, and online banking.
- Authentication Codes: Two-factor authentication codes sent via SMS, which can be used to bypass security measures.
- Contact Lists: Phone numbers and email addresses of contacts stored on the device, which can be used to launch further smishing attacks.
- Device Data: Location data, browsing history, call logs, text messages, and other data stored on the device.
Q3: What are the key signs that a text message might be a smishing attempt?
A3: Several red flags can indicate that a text message is a smishing attempt:
- Unknown Sender: The message is from an unknown or unfamiliar phone number.
- Suspicious Links: The message contains a link that looks suspicious or is shortened using a URL shortening service.
- Urgent Tone: The message creates a sense of urgency or alarm, pressuring you to act quickly.
- Grammatical Errors: The message contains grammatical errors, typos, or awkward phrasing.
- Requests for Personal Information: The message asks you to provide personal information, such as your bank account number or Social Security number.
- Too Good to Be True: The message offers something that seems too good to be true, such as a free gift or a large discount.
- Impersonation: The message impersonates a legitimate organization, such as a bank, government agency, or popular company.
- Unsolicited Contact: You did not initiate the communication with the purported sender.
Q4: What steps should I take if I accidentally clicked on a link in a suspicious text message?
A4: If you accidentally clicked on a link in a suspicious text message, take the following steps immediately:
- Do not enter any personal information: If the link led to a website, do not enter any personal information, such as your username, password, or credit card details.
- Close the browser window: Close the browser window or tab that opened when you clicked on the link.
- Run a malware scan: Run a full malware scan on your iPhone using a reputable antivirus app. While iOS is generally considered secure, it’s still possible for malware to be installed through vulnerabilities.
- Change your passwords: Change the passwords for all of your online accounts, especially those that you accessed on your iPhone.
- Contact your bank and credit card companies: Contact your bank and credit card companies to alert them to the potential fraud.
- Monitor your accounts: Monitor your bank accounts, credit card statements, and credit reports for any signs of unauthorized activity.
- Report the incident: Report the incident to the FBI’s Internet Crime Complaint Center (IC3).
- Consider a factory reset: As a last resort, if you suspect that your iPhone has been infected with malware, consider performing a factory reset. This will erase all data on your device, so be sure to back up any important information first.
Q5: How can businesses and organizations protect themselves from smishing attacks targeting their employees?
A5: Businesses and organizations can protect themselves from smishing attacks by implementing the following measures:
- Employee Training: Conduct regular training sessions to educate employees about the risks of smishing and how to identify and avoid these attacks.
- Security Policies: Develop and implement clear security policies regarding mobile device usage, data security, and incident response.
- Mobile Device Management (MDM): Implement MDM software to manage and secure employee mobile devices. MDM solutions can help to enforce security policies, install security updates, and remotely wipe devices if they are lost or stolen.
- Multi-Factor Authentication (MFA): Implement MFA for all critical systems and applications. This adds an extra layer of security that makes it more difficult for attackers to gain unauthorized access.
- Spam Filtering: Implement spam filtering solutions to block unwanted text messages from reaching employee devices.
- Incident Response Plan: Develop and implement an incident response plan that outlines the steps to be taken in the event of a smishing attack.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities in mobile device security.
- Simulated Phishing Attacks: Conduct simulated smishing attacks to test employee awareness and identify areas for improvement.
- Communicate Regularly: Keep employees informed about the latest smishing threats and provide them with ongoing security awareness training.
- Mobile Threat Defense (MTD): Consider deploying MTD solutions, which offer real-time protection against mobile threats, including smishing, malware, and network attacks. MTD platforms can detect and prevent malicious activity before it can compromise a device or network.